Genpact is a global firm specializing in professional services facilitating corporate transformations. The name “Genpact” signifies its mission of generating a significant impact. They lead the way in digital innovation and provide intelligent operations with a digital focus for their clients while driven by their mission to improve the world for people. Genpact is a driving force for large-scale real-world transformation, drawing from its extensive experience in reimagining and managing numerous processes for a diverse clientele, including many Global Fortune 500 companies. The company provides a positive work environment that promotes personal and professional growth for the Freshers jobs seekers.
Their approach involves design thinking, envisioning digital technologies, and using data and analytics to tackle complex challenges. They excel in connecting the dots, redefining processes, and reshaping the operations of businesses across the globe, spanning from New York to New Delhi and over thirty other nations. For those starting their career journey, Genpact offers an exceptional platform.
Given Genpact’s dynamic development landscape, young Software Engineers can gain valuable knowledge relatively quickly. Genpact maintains legacy code bases for its products but is also actively building new solutions using cutting-edge technologies. Therefore, working at Genpact can be highly advantageous for Software Engineers seeking engaging projects with a global impact. This blog will discuss genpact interview questions.
Eligibility Criteria
Candidates should review the specified eligibility criteria, including graduation, academic and general requirements, before initiating the Genpact Software Engineer Recruitment Process.
Graduation Criteria
Given below are the Graduation criteria for the Genpact Software Engineer Recruitment Process.
- A full-time B.E (Bachelor’s of Engineering) or a B.Tech (Bachelor’s of Technology) degree from a prominent university in any specialization like CSE/ECE/IT/EEE/TELECOM/EI.
- Master of Science (M.Sc) degree in Computer Science and Information Technology or other relevant field.
- Master of Technology (M.Tech) or Master of Engineering (M.E) in Computer Science and Information Technology or any other relevant stream.
- Bachelor’s of Computer Application (B.C.A) or Master of Computer Application (M.C.A).
Candidates should have scored above 60% and should have no backlogs.
Academic Criteria
The candidates should have scored at least 70% in their Senior Secondary or Diploma to be chosen in the genpact recruitment process.
General Criteria
To be hired in Genpact, a candidate requires specific general abilities. Listed below are the general criteria required to be hired by Genpact.
- Candidates must have excellent interpersonal & communication skills.
- Applicants must possess specific technical competencies.
- Professionalism in approach to work is essential. Strong organizational and detail-oriented abilities are required.
- Candidates should demonstrate the capability to comprehend and execute their tasks independently.
- Flexibility to work both day and night shifts is necessary.
You can visit Genpact Jobs for freshers and apply for new job openings.
Genpact Interview Process
Like any other digital business, Engineering teams play a vital role in achieving Genpact’s mission. So, Genpact always tried to develop their Technical team by hiring recent graduates and seasoned specialists for diverse internal developer job opportunities.
The genpact interview process is classified into 3 stages.
- The first round is online evaluation. Generally, the coding rounds will be conducted on portals such as Hackkerank, etc.
- The second round is the Technical Interviews.
- The final round is the Behavioral or Human Resources (HR) round.
Visit Freshers Jobs in Delhi to explore latest job openings.
Interview Rounds
The genpact interview process for freshers is similar to that of the Interview process for Experienced candidates. The only differences are the questions asked in the interview and the number of rounds. The recruitment process in Genpact is of 3 levels.
Online Evaluation Round/ Coding Round
The 1st round in Genpact is the Online Evaluation round, generally conducted on online platforms such as Hackkrank. HackerEarth, etc. In this round, the candidates will be given 2 -3 coding questions from topics like Data Structures and Algorithms and will be asked to give the solution codes for them. Apart from the coding questions, they will also give 10 – 20 Multiple Choice Questions from the fundamental concepts of Computer Science. Candidates must have a solid knowledge of Programming, subjects like DBMS (Database Management Systems), OS (Operating Systems), SQL, Computer Networks, OOP (Object – Oriented Programming) and specific programming languages like Java, C++, C, Javascript, etc. to excel in this round. This round consists of an elimination process, and candidates who perform well in both sections will be selected for the next round of the genpact recruitment process. The questions asked in both sections are of easy to medium complexity level, and candidates with knowledge of fundamental concepts of Computer Science can easily crack them.
Technical Interview Round
The next round is the Technical Round Interview. In this round, candidates will be asked 2 – 3 questions on Data Structures and Algorithms. They will also ask the candidates to provide the solutions for specific coding questions to assess their coding quality, code logic, etc. After that, they will give the candidates a set of technical questions to test their technical knowledge. Candidates can be asked to provide SQL queries to perform various operations on Relational Databases. They might also ask questions related to Cloud-based technologies. Knowledge of APIs (Application Programming Interfaces) functions and how distributed systems are designed are advantageous in the interviews. Questions about the candidate’s educational qualifications might be asked in this round. To crack this Genpact Technical Walk-in Interview round, the candidates must understand Computer Science’s fundamental concepts. Candidates should also have a solid grasp of Data structures, Algorithms, Database Management Systems (DBMS), and specific programming languages, like C++, Java, Python, etc. The interview panel will also ask questions from your resume, so be ready to answer those questions, too.
Human Resources (HR)/ Behavioral Round
The HR Interview is the final level of the genpact recruitment process. This round will check whether the candidate fits Genpact’s work culture. Questions related to puzzles will be asked to assess the general intelligence of the candidate. Situation-based questions will be asked to see how the candidate reacts to an awkward situation. The questions below are frequently asked in Genpact’s HR round.
- Could you please tell us about your strengths and weaknesses?
Strengths
Start the answer by explaining how your educational qualification is a strength for you. Showcase your genuine curiosity and acquire new skills. Explain how you can quickly adapt to a new work culture and your other skills that you consider your strength.
Weakness
Briefly explain what you consider to be your weaknesses and explain to them how you are trying to fix them.
- What do you know about Genpact?
This question allows you to express your knowledge about the company. Gather all the information you have collected during the company’s research and put them to good use. Talk about the latest technological advancements, etc., in that company.
- What value do you bring to Genpact, or explain why we should hire you?
In this question, you can explain what values you can bring to the company. This question is an opportunity to showcase your skills and abilities. Explain briefly about your skill sets and abilities that can be used to raise the company’s profit.
- Tell us about yourself
Start from your personal information, educational qualification, hobbies and interests, your passion for working in that specific company, etc. (Make sure that your answer is brief yet informative).
- Why do you want to work at Genpact?
In this question, you must discuss the benefits of working in that company. Talk about how your skill sets can be utilized better in this company.
- What are your Salary expectations?
This question is quite challenging but can be answered in a general phase. Explain how your skill sets can be helpful in this company, and you are perfectly fine with the regular income offered by the company for freshers.
Candidates who meet the eligibility criteria and possess excellent technical skills will most likely be recruited at Genpact, India. Now let’s delve into the frequently asked genpact interview questions in the Technical round.
Genpact Technical Questions
- Explain Multithreading in Operating Systems.
Multithreading is the ability of the CPU to run more than one thread of a code simultaneously with the support of the Operating system. Multithreading is different from Multiprocessing. In a Multithreaded application, threads share resources from one or more cores, like computational units, Translation Lookaside Buffer (TLB), or CPU caches. Multithreading tries to maximize the usage of one core by exploiting thread-level and instruction-level parallelism in multiprocessing systems with numerous complete processing units in one or more cores. Since both approaches are complementary, they are utilized in all modern system architectures that involve multithreading CPUs and cores.
- Explain the concept of Data Warehousing.
Data warehousing is collecting, extracting, processing, and importing data from several sources and storing it within a single database. A data warehouse can be explained as a central repository for data analytics that receives data from transactional systems and other relational databases. It is also defined as collecting historical data from an organization that aids decision-making. Data warehouse data is also used for data visualization, reporting, business intelligence, etc.
- Define Entities, EntityTypes, and Entity Sets in Database Management Systems.
- Entity: Entity is defined as a real-world object with attributes. Its function is to indicate the object’s qualities. For instance, a student, a teacher, or an employee represents an entity.
- Entity Type: Entity types are defined as entities with similar attributes. Entity types or attributes can be considered a trait that differentiates an entity from others. For instance, a student is an entity with a student id, name, etc.
- Entity Set: A collection of entities in a database that belongs to a specific entity type is known as an Entity set. For example, symbiosis is an entity set in a group of all students, employees, teachers, etc.
- What are Aggregation and Atomicity in Database Management Systems?
The definitions of the given terms are as given below:
- Aggregation: Aggregation is defined as a feature of the Entity Relationship model that permits a relationship set to interact with another relationship set.
- Atomicity: The atomicity attribute specifies whether an alteration made in the database is attached to all the rules. This results in the extension of one transaction’s failure to the failure of the whole transaction.
- What are Proactive, Retroactive and Simultaneous Updates in Database Management Systems?
- Proactive Updates: Proactive Updates are modifications made to the database before it enters into usage in the real world.
- Retroactive Updates: Retroactive Updates are applied to a database once it is operational in the actual world.
- Simultaneous Updates: Simultaneous Updates are applied to the database simultaneously as they become effective in the real world.
- What are the Intension and Extension in Database Management Systems?
- Intension: Intension, also known as the Database Schema, is the term used to describe the structure and design of a database. This database scheme is established during the initial database design phase and typically remains relatively unchanged.
- Extension: Extension, on the other hand, refers to the number of data rows or tuples present in the database at any given moment. This value varies as new tuples are added, existing ones are updated, or some are removed. Therefore, the data in the database at a specific time is referred to as the database’s extension or, more broadly, as the database’s snapshot.
- Define Index Hunting and explain its functions in Database Management Systems.
Index hunting is defined as the process of improving a collection of indices. The primary purpose of Index hunting is that the index enhances the query performance and reduces the time taken for a query process. Given below are different ways in which Index hunting enhances the query performance.
- Most probably, the optimal queries are suggested along with the usage of the query optimizer.
- It checks the effect of using index, query distribution, and performance measurements.
- For specific problem queries, optimization is also performed within the databases.
- Explain Threads in Operating Systems.
A thread is a single flow of task execution in a process. It is otherwise called a thread of execution or control. Thread execution can be performed within the process of any operating system. Apart from that, multiple threads can exist within a single process. Each thread of the same process utilizes a distinct program counter, a stack of activation records, and control blocks. Threading is always defined as a light technique. It is possible to break down a process into multiple threads. MS Word uses multiple threads to prepare the text in a single thread, then receives input using another thread, etc. A thread is considered to be a single stream within a process. Each thread is unique and consists of the components following them.
- A counter for a program.
- A series of registers.
- A stacking area.
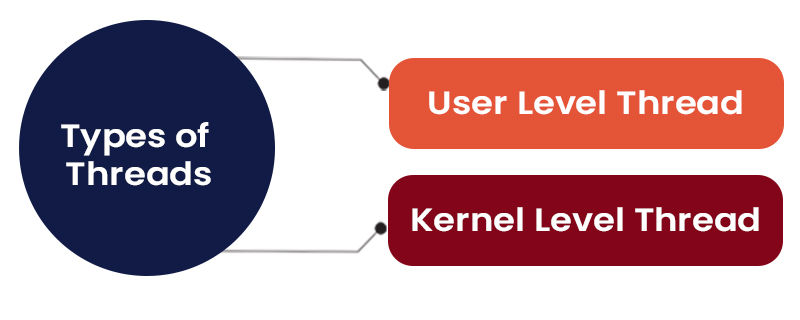
Threads share codes, data, and other Operating System resources. So, they are not self-contained. Threads are classified into 2 types.
- User Level Thread (ULT): User Level Threads are created in the user-level library without relying on system functions. Switching between threads doesn’t require interaction with the Operating System or a kernel interrupt. The kernel does not know about user-level threads and treats them as single-threaded processes.
- Kernel Level Thread (KLT): The management of threads is the responsibility of Kernel Level Thread (KLT). Instead of each process maintaining its thread table, the kernel maintains a central thread table that monitors all threads in the system. Additionally, the Kernel Level Thread monitors processes using the standard process table. The operating system’s kernel features are dedicated to creating and administering threads.
Some genpact interview questions will also include examples.
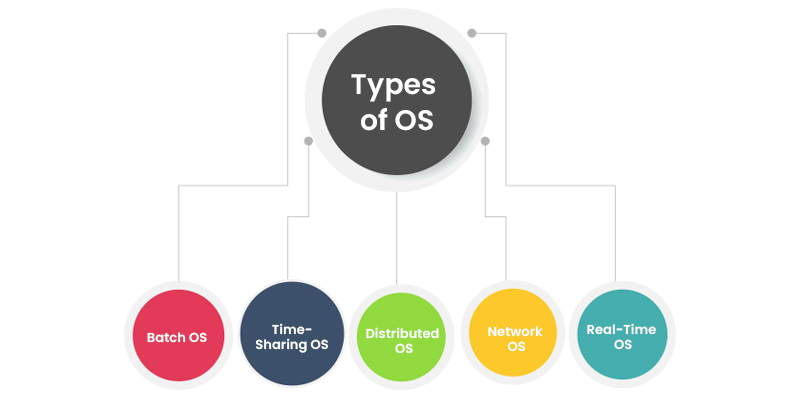
- List a few OS (Operating Systems) you know with examples.
The following are the types of OS (Operating Systems) I know.
- Batch Operating System: It is a computer program that is used to sequence jobs without any requirement of human interactions automatically.
- Time-Sharing Operating System: People can share computer resources using a Time-Sharing Operating System. Since many people share computer resources, there will be an increased resource usage in this type of OS.
- Distributed Operating Systems: DOS (Distributed Operating System) is software for managing multiple computers.
- Network Operating System: Network Operating System is mainly used for security purposes since it is possible to connect various computer’s operating systems to one network with the help of this type of Operating System.
- Real-Time Operating Systems: RTOS (Real-Time Operating Systems) are used to accept multiple events that happen external to the system in a short period or under tight deadlines. This type of OS includes Industrial control, telephone switching equipment, aircraft control, real-time simulations, etc.
Some examples of Operating Systems are given below:
- Windows are used for Graphical User Interface Operating System based on Personal Computers.
- GNU or Linux are used in Personal Computers, File and Print servers, Workstations, ISPs, Three-tier Clients and Servers.
- iOS is used in Apple’s OS for iPhone, iPad, and iPod Touch.
- macOS is used for Apple’s Personal Computers and Workstations like MacBook, iMac, etc.
- Android is used for Google’s Operating System for Google’s smartphones, tablets, smartwatches, etc.
- Explain the various types of Real-Time Operating Systems.
A Real-Time Operating System is a system that operates under real-time constraints, ensuring that responses are delivered within set time limits or under specific deadlines provided. For example, a flight control system, Real-Time monitoring, etc. Given below are the types of Real-time systems with timing constraints.
- Hard Real-Time Operating System: This type of Real-Time Operating system will always meet deadlines. The outcomes of failing to meet a deadline can be disastrous. In the case of a hard real-time system, any increase in lateness can cause a rapid deterioration in the system’s output, potentially turning it negative. Lateness indicates how a real-time system performs a task later than its deadline. A flight control system serves as an illustrative example.
- Soft Real-Time Operating System: Soft Real-Time Operating Systems can sometimes miss deadlines. Unlike Hard Real-Time Operating Systems, it won’t result in disastrous consequences if you miss the deadline. As the lateness increases, the deterioration of the system’s output reduces. Switches on mobile phones are examples of this type of Real-Time Operating System.
- List out the benefits of thread over processes.
The benefits of thread over processes are listed below:
- Faster thread context switching: Thread context switching is much faster when compared to process context switching. A higher CPU overhead is necessary due to the requirement for a process context shift.
- Responsiveness: It is possible to return the output of a single thread when it completes its execution if the process is broken into numerous threads.
- Resource sharing: It is possible to share code, data, and files throughout all threads within a process. It is imperative to notice that sharing stack and register between the threads is impossible. A thread will have its registers and stack.
- Effective multiprocessor system utilization: If one process contains several threads, scheduling numerous threads on multiple processors is possible. As a result of this approach, the process will take less time to run.
- Increased System Throughput: When a process is broken into numerous threads, each thread will be considered a single task, and the number of jobs performed per unit of time will increase. As a result, the system’s throughput will be boosted.
- Communication: Communication between the threads becomes easy since they share a similar address space. To communicate between the 2 processes, we must take a unique communication approach during the process.
- List a few advantages and disadvantages of User Level Threads.
Advantages of User-Level Threads:
- It is easy to implement User-level Threads over Kernel threads.
- Unlike Kernel-level threading, Operating systems support User-level threading.
- User-level threading is faster and more efficient. When compared to Kernel-level threads, Context switch times are shorter.
- User-level threads do not necessitate any modifications to the operating system, and the representation of threads at the user level is more effortless.
- The user-level process address space stores small registers, PCs, stacks, and flow control blocks.
- Creating, modifying, and synchronizing streams without process intervention will be accessible in user-level threading.
Disadvantages of User-level Threads:
- There needs to be more coordination between user-level threads and the kernel.
- The entire process will be blocked if there is any page fault in a single thread.
- List out a few benefits and drawbacks of Kernel Level Threads.
Benefits of kernel-level threads:
- Kernel-level threads can manage and schedule all threads.
- The scheduler might allocate additional CPU time to a heavily threaded process.
- Kernel-level threads are well-suited for latency-sensitive applications.
Drawbacks of Kernel Level threads:
- Implementing kernel threads is more complex than implementing user-level threads.
- Kernel-level threads typically exhibit slower performance compared to user-level threads.
- List the benefits of using views in a Database Management System.
Listed below are some advantages of using views in a Database Management System.
- It is possible to represent a subset of data in a table using views. As its outcome, a view can act as a means to restrict the level to which the underlying tables are exposed to external users. It enables users to query the view without providing access to the whole base of the database. This process offers data security and control, allowing you to present specific data while keeping the underlying details concealed selectively.
- Views can serve as aggregated tables, where the database engine performs data aggregation operations like sum or average and then presents the resulting data alongside the original dataset. This approach simplifies data analysis and reporting.
- Views enable combining and simplifying multiple tables into a single virtual table. This approach simplifies querying and reporting by abstracting the underlying database structure.
- Views need more storage space. The database only maintains the definition of the view, not a duplicate of all the data it references. This process makes them an efficient way to manage and manipulate data.
- Views can obscure data complexity by presenting a simplified, user-friendly interface to the data. They hide the underlying schema details, making it easier for users to work with the database.
- Depending on the SQL engine and database system used, views can provide additional security benefits. They can be used to restrict access to specific columns or rows, effectively limiting what users can see and manipulate.
- List down a few advantages of using C++.
- Given below are the advantages of using C++:
- C++ preserves all the C language parts and also simplifies the memory management.
- Applying C++ code on any platform is easy since it is highly portable.
- C++, an object-oriented programming language, incorporates concepts like classes, objects, inheritance, polymorphism, and abstraction.
- In C++, inheritance allows for the removal of redundant code and the reuse of existing classes.
- Data hiding is vital in helping programmers create secure applications resistant to intrusion.
- Message passing serves as a communication method that enables objects to interact with each other.
- C++ boasts an extensive library of functions.
- State the merits and demerits of using Object Oriented Programming Languages.
Given below are the advantages of using Object-Oriented Programming Languages.
- Object Oriented Programming Languages enable programmers to simulate the real world and its entities since they follow a bottom-up approach.
- It enables code reusability.
- Through the use of abstraction, the user is prevented from unnecessary data exposure.
- Designing in Object-Oriented Programming languages necessitates a comprehensive and extended design phase, resulting in improved designs with fewer flaws.
- Object-oriented programming languages facilitate decomposing significant problems into smaller, manageable components.
- Programmers can expedite the achievement of their goals through the adoption of Object-Oriented Programming languages.
- The use of Object-Oriented Programming languages results in reduced code complexity for developers.
- Object-oriented programming languages allow easy code redesign and extension without impacting other functionalities.
Given below are the disadvantages of using Object-Oriented Programming Languages.
- Extensive planning is often necessary for effective utilization of these languages.
- There’s a tendency for classes to become overly generalized in Object-Oriented Programming languages.
- They may not be suitable for solving small-scale problems as they can introduce unnecessary complexity.
- In some cases, programs written in Object-Oriented Programming languages may consume excessive memory, which is undesirable.
Some genpact interview questions regarding a specific concept’s types, levels, properties/ characteristics, or components will be asked.
- Explain the concept of Data Independence and its types.
Data Independence prevents the change in data at one level of DBMS’s three-tier architecture from influencing data at another level. Data Independence is classified into 2 types.
- Physical Data Independence: Physical Data Independence alters the physical location of tables and indexes and should not affect the conceptual level or the external presentation of data. This type of data independence is relatively simple to attain and is upheld by most Database Management Systems.
- Conceptual Data Independence: The data should be independent in conceptual Data Independence. Accordingly, any modifications made to the conceptual schema will not impact the external schema. For instance, when adding or removing attributes from a table, there should be no impact on how the table appears to the user. Unlike physical data independence, achieving this kind of independence is more challenging, as alterations to the conceptual schema are reflected in the user’s perspective.
- Explain the properties of ACID in Database Management Systems.
ACID generally stands for Atomicity, Consistency, Isolation, and Durability. Sometimes, a transaction is a logical unit of work used to read and update the database contents. Transactions make use of read-and-write operations for accessing data. Specific properties are followed before and after a transaction for database maintenance. These properties are known as ACID properties. Given below are the characteristics of ACID.
Atomicity: If a transaction happens all at once or doesn’t even occur, it is said to be atomic. If there are no traces of any transaction steps, then it is considered as there are no intermediate grounds. Whether a transaction is complete or not, it is always viewed as a single entity.
- Abort: Any database updates made are discarded or rolled back if a transaction aborts. In other words, none of the changes are permanently saved to the database.
- Commit: When a transaction is committed, it implies that the changes made during the transaction are finalized and become visible to other transactions. These changes are now considered a permanent part of the database.
Consistency: It is vital to maintain the integrity constraints before and after the transaction to ensure the consistency of the database.
- Before the transaction (T), the total is 500 + 200 = 700.
- After the transaction (T), the total is 400 + 300 = 700.
Consequently, the database is maintained in an orderly manner. Inconsistencies arise when T1 succeeds but T2 fails, resulting in an incomplete state for T.
Isolation: Isolation property is used to run multiple transactions concurrently without creating inconsistencies in the state of the database. Transactions take place in a non-disruptive manner. Changes occurring in one transaction will be visible to other transactions once the changes done are put to memory or committed. The features ensure that the transactions that are concurrently running provide a similar state to the substantially running transactions.
Durability: Durability always ensures that the updates and modifications done in the database are stored and written to disk after concluding the transaction and that data survives even after the system failure. These modifications are recorded permanently in the nonvolatile memory. As an outcome, the effects of the transaction will not be erased.
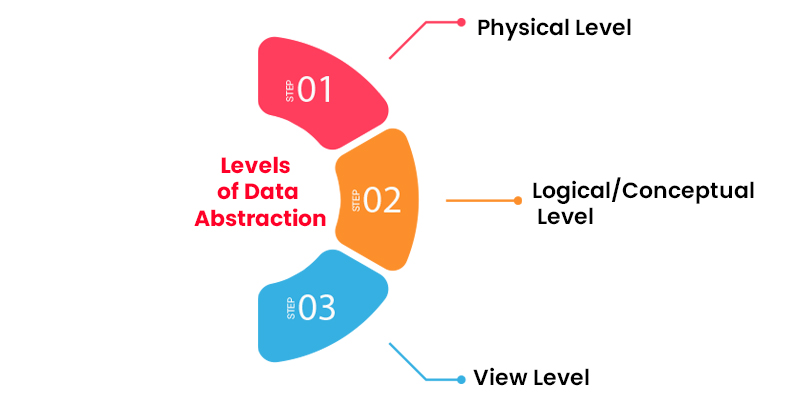
- List out the levels of data abstraction in Database Management Systems.
In Database Management Systems, there are three fundamental levels of data abstraction.
- Physical Level: This level of data abstraction indicates how the data are stored. It is the lowest degree of data abstraction.
- Logical or Conceptual Level: The next level is the Logical or Conceptual level, which decides which data is stored in the database and how the data pieces are related.
- View Level: View level is the most significant level of data abstraction, and it describes only a portion of the whole database.
- Explain transactions in SQL and its Properties.
A transaction is described as a logical unit of work done on the database. Transactions are logically ordered work sequences that a database application can complete manually or automatically. A transaction is a propagation of one or more modifications done to the database. For example, creating, deleting, or updating a record from a table is known as completing a transaction on the table. Keeping track of these transactions is vital to prevent data integrity and address database issues. Collecting and running numerous SQL queries simultaneously is part of the transaction. Transaction in SQL consists of 4 standard qualities, generally known as ACID.
- Atomicity: Atomicity aims to check whether the processes are completed successfully inside the work. If not, the process will be considered a failure, the transaction will be aborted, and the preceding activities will be reserved.
- Consistency: The purpose of consistency is to check whether the changes done on the database state not or adequate once a transaction is committed successfully,
- Isolation: Isolation ensures that transactions can run independently of each other while maintaining transparency to them.
- Durability: It ensures the transaction’s effect or outcome is secured during a system failure.
Some genpact interview questions will also involve syntaxes or codings.
- Explain Database objects in Database Management Systems.
A database is an object defined in a database. It is used to store or refer data. All objects generated through the create command are called database objects, serving as containers for data storage and manipulation. Here are a few illustrations of database objects:
Table:
The table acts as a primary storage container with compound rows and columns. Given below is the syntax for creating a Table.
CREATE TABLE [schema.]table
(
column1 datatype1 [DEFAULT expr1],
column2 datatype2 [DEFAULT expr2],
…
);
Views:
Views, in the context of a database, serve as a logical representation of data subsets derived from one or more tables. A view can be considered a virtual table that derives data from another view or an underlying table. While it provides a way to view and, in some cases, update data, it doesn’t store any of its own. The tables on which a view is constructed are known as base tables. A view is saved in a database’s data dictionary as a SELECT statement. Given below is the syntax for creating a View:
CREATE OR REPLACE FORCE|NOFORCE VIEW view
AS
subquery
WITH CHECK OPTION [CONSTRAINT constraint]
WITH READ ONLY [CONSTRAINT constraint]
[WITH [CASCADED|LOCAL] CHECK OPTION];
Sequence:
Within databases, sequences are utilized for generating primary fundamental values. They are a type of database object created by a user and can be utilized by multiple users to generate unique integer values. Sequences are commonly used for generating primary fundamental values, ensuring each row has a unique identifier. An internal Oracle routine generates and increments (or decrements) these sequence values. Given below is the syntax for creating a Sequence:
CREATE SEQUENCE sequence
START WITH n
INCREMENT BY n
MINVALUE n
MAXVALUE n
CYCLE | NOCYCLE
CACHE n | NOCACHE;
Index:
Indexes play a vital role in enhancing query performance in the databases. This database object is employed to establish an index within the database, serving as a schema object that can expedite the retrieval of rows by utilizing a pointer. Indexes can be created explicitly or automatically; their absence on a column may result in full table scans. They offer rapid, direct access to table rows to minimize disk Input and Output operations by providing an indexed path to locate data swiftly. The database server automatically employs and maintains the index, necessitating no direct user intervention after its creation. Importantly, indexes are logically and physically separate from the tables they index, allowing them to be generated or removed at any time without affecting the base tables or other indexes. Given below is the syntax for creating an Index.
CREATE INDEX index
ON table
(column[, column]…);
Synonyms:
Synonyms, as a database object, are primarily utilized to simplify database access by creating an alternative name for an object. They make referencing tables other users own more convenient and shorten lengthy object names. When referring to a table owned by another user, you typically need to prefix the table name with the creator’s name followed by a period. Creating a synonym for a table, view, sequence, procedure, or any other object eliminates the necessity to qualify the object name with the schema. It provides an alternate, more concise name. This approach is advantageous when dealing with lengthy object names, such as views.
In terms of syntax, the meanings of various elements are as follows:
- PUBLIC: It designates the creation of a synonym that is accessible to all users.
- SYNONYM: This is the name of the synonym being created.
- OBJECT: It specifies the object for which the synonym is being created.
Given below is the syntax for creating Synonyms.
CREATE [PUBLIC] SYNONYM synonym
AS object;
- What are Subqueries in SQL? Write down an SQL query for the given table of employees to find all the employees with salaries greater than five thousand.
A subquery is referred to as a query inside another query that is used to retrieve data or information from the database. The query outside the subquery is known as the main query. Subqueries will be processed initially, and their results will be passed to the main query. It can be nested into any query, like SELECT, UPDATE, or OTHER. Any comparison operators, like >, =, can be utilized in a subquery. The syntax for a subquery in SQL is as follows.
SELECT tableOne.columnName, tableTwo.columnName
FROM table one
JOIN tableTwo ON tableOne.columnName OPERATOR tableTwo.columnName
WHERE [optional additional conditions]
Below is a SQL query code using subqueries to find all the employees with more than five thousand salaries in the employee’s table.
SELECT e.*
FROM EMPLOYEES e
JOIN (
SELECT EMPLOYEE_ID
FROM EMPLOYEES
WHERE SALARY > 4500
) subquery
ON e.EMPLOYEE_ID = subquery.EMPLOYEE_ID;
Some genpact interview questions will be asked in the form of an explanation.
- Explain Object Oriented Programming Languages. Is Java one a Pure Object Oriented Programming Language? If not, justify why?
If everything in the program is considered an object, then that programming language is purely object-oriented. This type of program doesn’t support primitive types. This type of program should satisfy the properties given below.
Encapsulation: Encapsulation is the wrapping up of the data members and member functions as a single entity. In encapsulation, data and the functions that alter the data will be bound together in OOPS. Let’s look into an actual world example for this case: A company consists of diverse departments, like accounting, finance, and sales, to name a few. The Finance department will handle the financial transactions and continuously check all the financial data. The sales department is in charge of the activities related to sales. The sales data will be requested for a particular month by an official from the finance department. The finance official is not permitted to access the data from the sales department directly. The officials from both departments should speak about it, and the finance official has to request the sales official to deliver the required information. This concept is known as encapsulation. The data from one department is hidden from other departments for security purposes.
Inheritance: Inheritance is the capacity of a class to derive features or traits from another class. It is one of the most significant characteristics of Object-Oriented Programming.
- Subclass of Derived Class: A class is used to inherit the properties from another class.
- Base Class or Super Class: A base is a class from which the other class inherits the properties.
- Inheritance facilitates the principle of “reusability,” allowing us to create a new class based on an existing one that already contains some of the required code. This way, we can inherit the fields and functions of the original class. For instance, Dog, Cat, and Cow are examples of classes derived from the Animal base class.
Polymorphism: Polymorphism is an ability that enables a message to be displayed in multiple formats. Simultaneously, an individual can possess multiple characteristics. They can be a father, a spouse, and a worker all at once. Consequently, the same individual may exhibit distinct behaviors in varying contexts. This phenomenon is called polymorphism, where an operation may exhibit different behaviors in different situations. The behavior is contingent upon the data types employed in operation. C++ supports polymorphism through features like operator and function overloading.
- Operator Overloading: The purpose of operator overloading is to force an operator to function differently in various situations.
- Function Overloading: Function overloading uses a single function name to accomplish many tasks. Inheritance is mainly implemented using polymorphism.
An example of Polymorphism is given below:
Let’s imagine a situation where we have to create a function for adding integers, and there are cases where we need to add two integers, while in other situations, we need to add three integers. We can define a method named “sum” with the same name but different parameters, and the proper method will be called based on the parameters provided.
Abstraction: Data Abstraction is considered one of the most fundamental characteristics of object-oriented programming in C++. Abstraction is known as revealing only the required or essential information while hiding the rest of the details. Data abstraction involves revealing only the essential characteristics of the data to the external environment while hiding the implementation details.
Let’s consider the case of a person at the wheel of a car. If the person only knows to press the accelerator, it will increase the car’s speed. But if that person knows how to apply the brakes, they will stop the car. However, they might need to learn the car’s internal mechanisms or how its accelerator, brakes, and other controls are physically implemented. This phenomenon is known as abstraction.
There are two ways to Abstraction:
- Abstraction using Classes: In C++, we can implement abstraction using classes. Through the use of access specifiers, a class helps us organize data members and member functions. A class can control which data members are visible to the external world and remain hidden.
- Abstraction in Header Files: Another form of abstraction in C++ can be achieved through header files. Take, for instance, the pow() function in the math.h header file. When we need to calculate the power of a number, we simply call the pow() function from the math.h header file and provide the numbers as arguments without needing to understand the underlying algorithm used by the function to compute the power of numbers.
Since predefined data types are not objects in Java, it is not a pure object-oriented programming language.
In conclusion, preparing for Genpact Technical Interview questions requires basic computer science concepts and insight-based topics like Data Structures, Algorithms, APIs, Cloud-based technologies, SQL queries, Database Management Systems, and specific programming languages like Java, Python, and C++. In this blog, we explored frequently asked genpact interview questions.